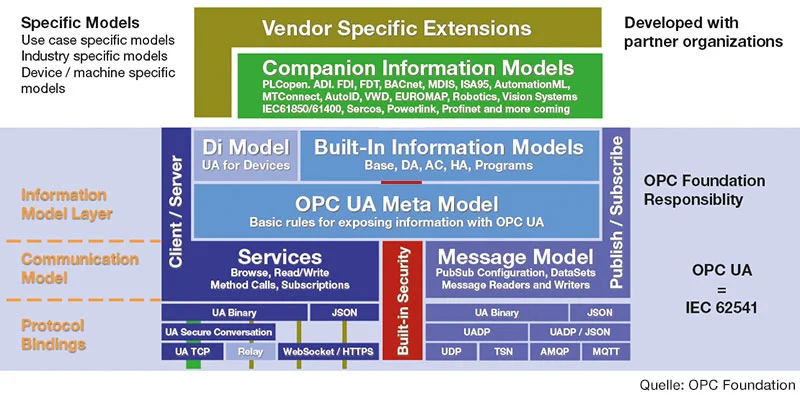
OPC UA(OpenPlatformCommunicationsUnified Architecture) is a platform-independent and service-oriented architecture that makes it possible not only to transport machine data, but also to describe it semantically. It represents a uniform standard for data and information exchange. The first version of OPC UA was published in 2006 and a revised version in 2008 as an extension of OPC Classic, which is no longer based on Microsoft DCOM technology. The basic principles behind this new architecture are the provision of simple interfaces, a standardized message format, flexible expansion options and the implementation of high security standards. OPC UA therefore offers an architecture that can adapt quickly and easily to the ongoing development of industrial automation. OPC UA can therefore be used on any operating system - from the sensor to the cloud. Semantics are used to describe the transferred data in order to significantly simplify integration. The manufacturer-independent exchange of information makes OPC UA a particularly important building block for Industry 4.0.
Physics / Topology
OPC UA uses a TCP-based, optimized, binary protocol, which has been assigned port 4840 by IANA. This binary data exchange was prescribed by the OPC UA specification and is therefore supported by every OPC UA application.
Another protocol used is WebService. WebServices supports the HTTP or HTTPS transport protocol, which have also been assigned to prescribed ports, port 80 and port 443.
The OPC UA architecture works according to the client-server principle. The OPC UA server provides data and information, which an OPC UA client can then access by reading or writing it. A system can be both server and client at the same time.
Another communication model used by OPC UA is Publish/Subscribe. This model provides a mechanism for many-to-many configurations in which information is not exchanged directly, but transmitted to a broker, which then forwards it. In general, it should be noted that at least one IP network is required for the operation of OPC UA.

In addition to the mandatory IP address or device name for addressing.
The network can be searched for available OPC UA servers via the local discovery server (usually a function of the OPC UA client).
Part of the connection configuration is also the optional connection protection, which can be carried out in different ways and is device-dependent. You can choose whether you want to establish an authenticated, signed and encrypted connection, depending on how secure the transmission is.
Further configuration on the OPC client side is largely automatic, as the identification, functional scope, data structure and technical limitations of the devices are read out, after which the desired data tags can be selected.
The OPC UA Companion implementation can be used to generate device models in order to achieve a high degree of interoperability. The data models of certain device types are standardized and various device profiles define the implemented range of functions.
Cybersecurity

An important advantage of data transmission via OPC UA is the cyber security provided by the latest technologies. Especially when data is not only transmitted locally at the site via various networks but also via the Internet.
The security concept covers the trustworthiness of information in terms of confidentiality, integrity and availability. It also includes access control with authentication, authorization and auditability. x.509 public key infrastructure, for example, is used to authenticate and authorize devices and users. Alternatively via a WS-Security token.
OPC UA messages can be encrypted and signed to ensure integrity so that no manipulation of data is possible. Invalid messages from a denial of service attack (DDoS) on OPC UA servers, for example, are immediately discarded to avoid tying up computing power.
Variants / Versions

Version 1.04
Implementation of the Pub/Sub communication model, whereby the number of communication partners can be increased and a direct connection is no longer required.
With the help of the JSON Web Token, OAuth2, user identification of cloud platforms such as Azure, Google, etc. can be mapped.
Reverse connectivity makes it possible to establish a connection from servers behind a firewall.
New security guidelines enable the use of the current cryptographic hash function, SHA 256.
Areas of application
OPC UA is used in the manufacturing, oil & gas, building automation, pharmaceutical and many other industries.
Remote maintenance
Modular remote maintenance and M2M router Ewon Flexy for remote maintenance and data services
HMI and IIoT edge Gateways
The smart HMIs of the cMT series - Server / Client HMI architecture - High flexibility and strong improvement in work efficiency.
Industrial panel PCs, displays and box PCs
Connectivity, performance and application options at all levels. From entry-level to high-end platforms for advanced applications. A complete range of IPCs that meet all the requirements of field applications.